p5. The patch was backported.
fmstrat
For a long time I've been considering carrying "parking is hard" cards for windshields.
We aim to introduce additional paid services (not paywalled features, as we will never implement paywalled features), which will help support the project and that enhance self-hosting, making it easier and more reliable. First among the many services already planned is an end-to-end encrypted, off-site backup and restore feature, built directly into Immich. This will enable a buddy backup feature as well.
I love this.
Free features, but offering actual useful services for self-hosters (encrypted cloud backup). Great business model for a project like this.
What is the show?
I mean, Bernie probably isn't the guy to be complaining about.
Yea this is satire, it should be moderated out of pcgaming.
The FedID is just a way to try out federated services internally. Ghost can federate posts to other federated services, they have plenty of info on their site if you're interested.
I was thinking the same thing. Sounds like they did exactly what any studio would do in a regular shoot.
Dropbear. You can run a small SSH server in initd that allows you to SSH in and type the encryption password. It doesn't run a shell, just cryptsetup.

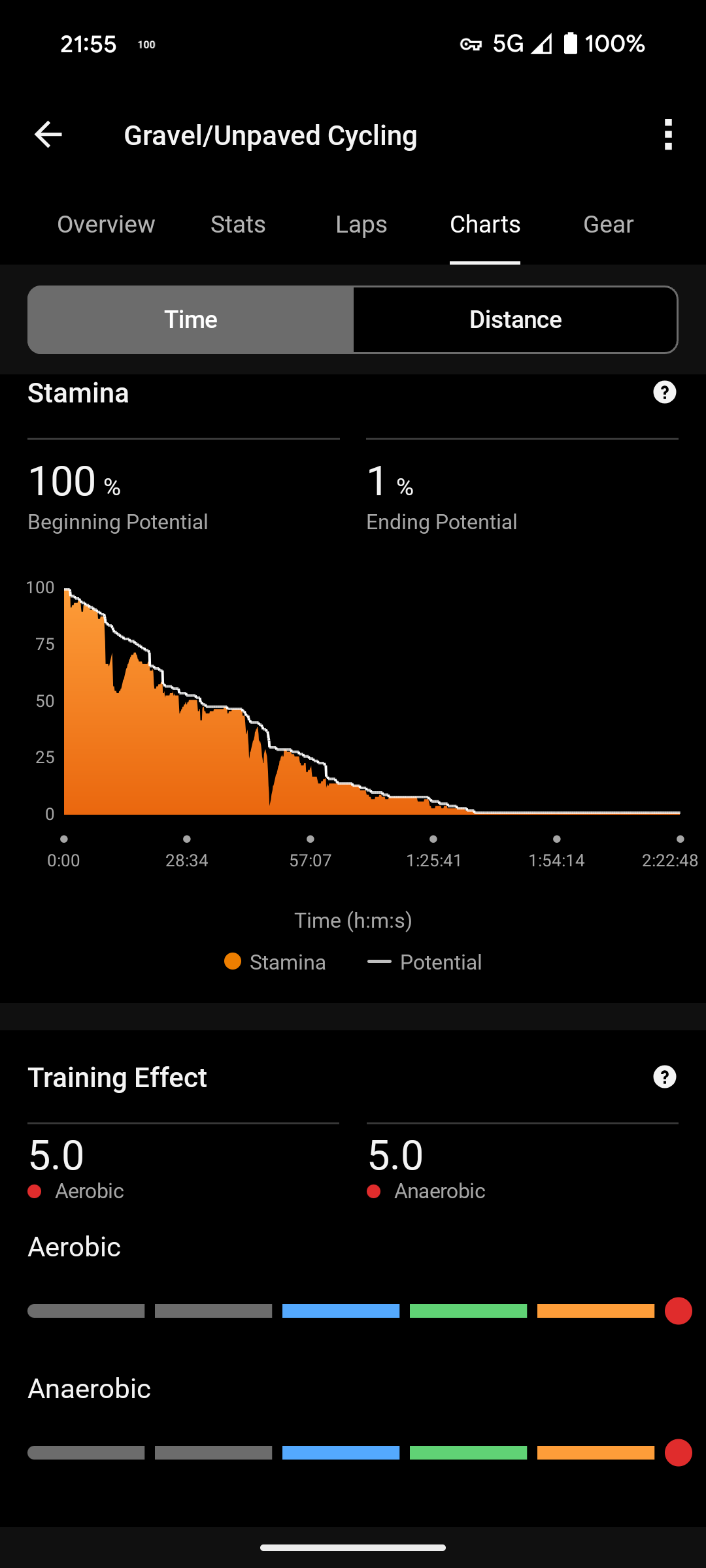
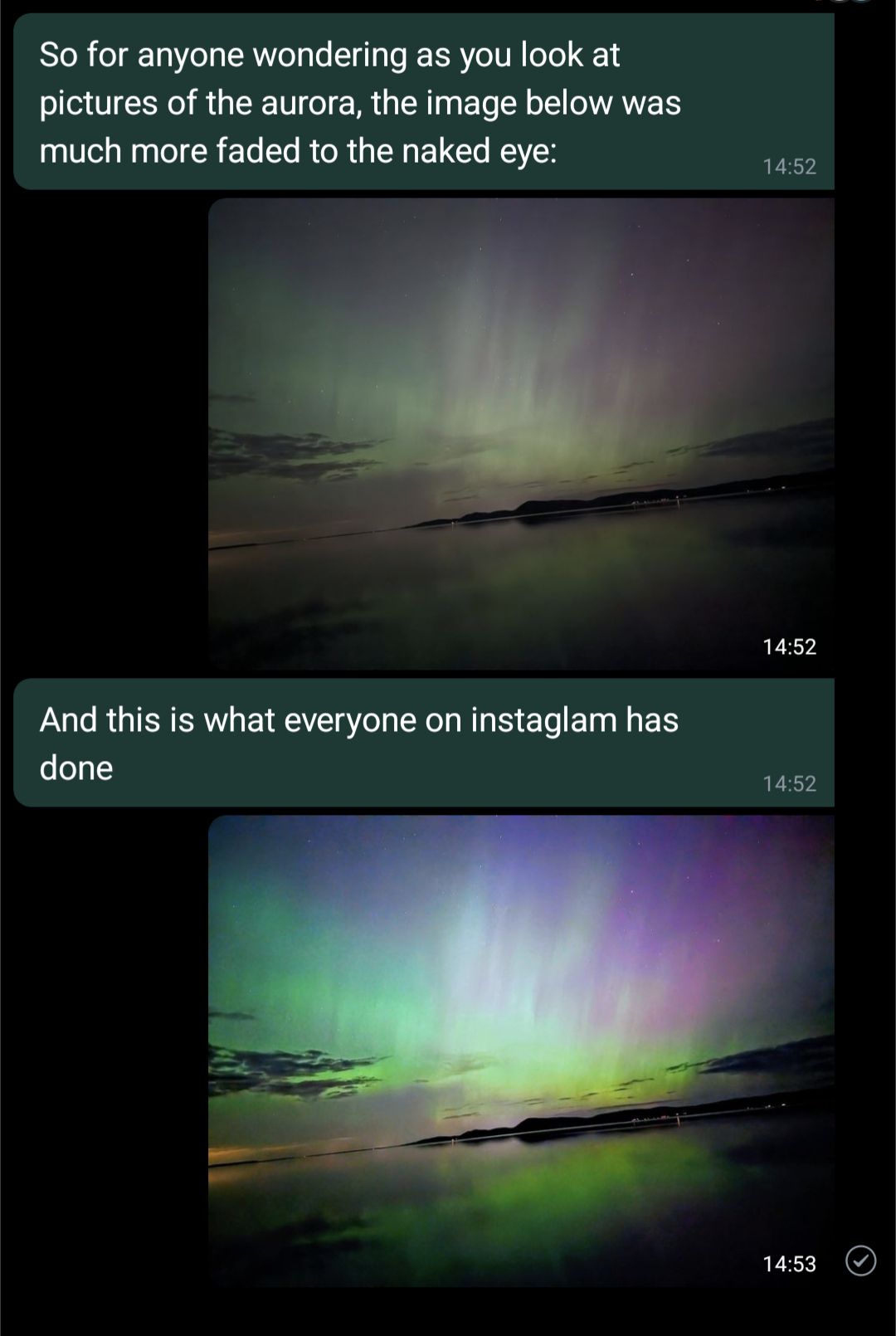
Best part: