It's not so easy to ban VPNs. They need to setup DPI everywhere. And then people will start using DPI circumvention software.
Technology
This is a most excellent place for technology news and articles.
Our Rules
- Follow the lemmy.world rules.
- Only tech related news or articles.
- Be excellent to each other!
- Mod approved content bots can post up to 10 articles per day.
- Threads asking for personal tech support may be deleted.
- Politics threads may be removed.
- No memes allowed as posts, OK to post as comments.
- Only approved bots from the list below, this includes using AI responses and summaries. To ask if your bot can be added please contact a mod.
- Check for duplicates before posting, duplicates may be removed
- Accounts 7 days and younger will have their posts automatically removed.
Approved Bots
Man I can't follow UK politics. I thought Labour was a progressive party
Geeze I hope I don't...slap tailscale on a vps
Can't wait for the next election to kick out the Tories so can roll back all their draconian bills.
I don't think it's even possible to get rid of VPNs without outright banning encryption. If I set up a VPN that uses an obscure port and the traffic is encrypted, how are they going to know it's even a VPN?
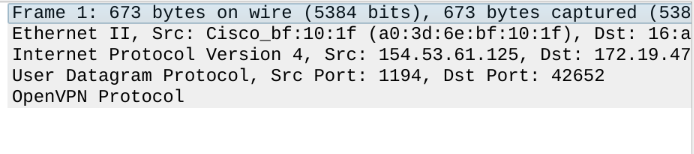
Attached below is a Wireshark trace I obtained by sniffing my own network traffic.
I want to draw your attention to this part in particular:
Underneath "User Datagram Protocol", you can see the words "OpenVPN Protocol". So anyone who sniffs my traffic on the wire can see exactly the same thing that I can. While they can't read the contents of the payload, they can tell that it's OpenVPN traffic because the headers are not encrypted. So if a router wanted to block OpenVPN traffic, all they would have to do is drop this packet. It's a similar story for Wireguard packets. An attacker can read the unencrypted headers and learn
- The size of the transmission
- The source and destination IP addresses by reading the IP header
- The source and destination ports numbers by reading the TCP or UDP headers
- The underlying layers, up until the point it hits an encrypted protocol (such as OpenVPN, TLS, or SSH)
Download Tor, Whonix & Tails