So how do I see the boobs
Mildly Interesting
This is for strictly mildly interesting material. If it's too interesting, it doesn't belong. If it's not interesting, it doesn't belong.
This is obviously an objective criteria, so the mods are always right. Or maybe mildly right? Ahh.. what do we know?
Just post some stuff and don't spam.
You put on your robe and wizard hat
Goddamn old people.
Wait. I get that reference. Does that mean I'm an old people?
Unfortunately. You'll be in the retirement home before you know it with the rest of us.
Old men are the future!
I don't think that's accurate.
The future is now old men!
Send bob and vagene
Sorry, they're in Scunthorpe right now.
I'm lookin at one right now
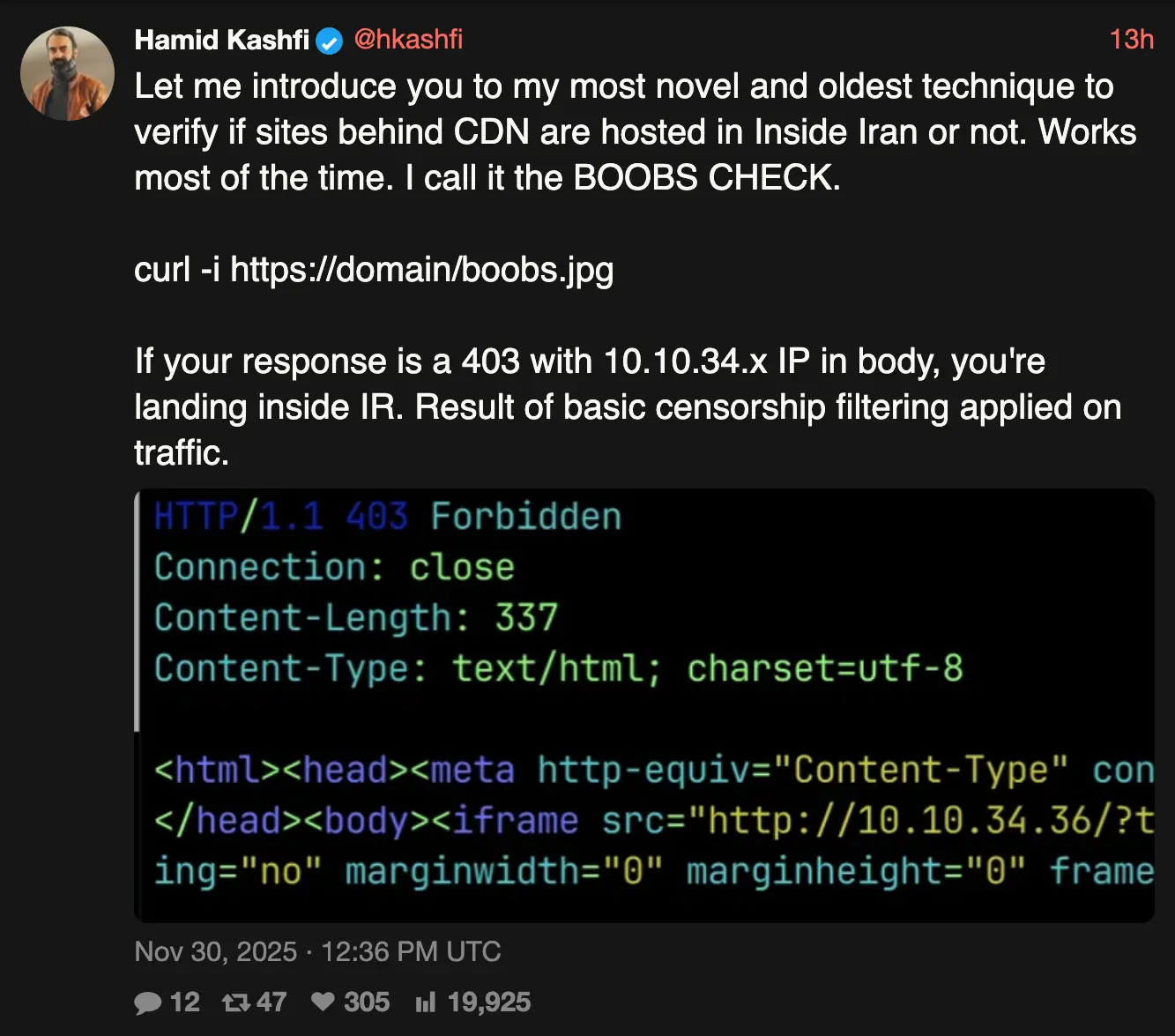
Also don't be in Iran
You really need to get out of Iran.
I dunno, but if you find out, let me know.
My original guess was that they're intercepting DNS, but since boobs is in the path, it wouldn't be sent. How does this work?
They are giving response codes like 403 so it's not a failure to resolve and I agree it's not DNS... It's behaving differently based on different sub pages so it's something underneath the https encryption. Maybe an intermediary WAF that decrypts? Maybe some weird server side tooling that has govt provided?
I would guess WAF but I'd love to hear from someone who actually knows.
It’s either
- Client side ssl forward proxy (MitM cert installed on client)
- in-line decryption in the server
- client side software
- tls downgrade
- cert authority compromise
Right? If it were an unencrypted HTTP GET request, then every router on the way would see the plaintext string boobs in the URL and therefore intercept it.
If I had to guess, Iran has so few landline connections that they man-in-the-middle every TLS connection they can by either forcing every server to hand over their private key files (difficult) or by forcing a certificate authority trusted by default Web browsers (there's a lot of them) to issue certificates for every top level domain they see in SNI data attached to encrypted packet headers; the latter method need not even require participation by Iranian servers, so long as the traffic is bottlenecked for man-in-the-middle attacks and outsiders don't question unusual certificate authorities being used.
Why are you posting your own version of the exact same screenshot?
Saves a click?
I dont see a screenshot.
exactly, there is no screenshot and I don't want anyone to need to go to the website
So the solution to "I use a bad app" is comment spam?
And why not repost the OP image? They went and took their own screenshot of the tweet. Why take your own? What if they'd edited it? I know it's nothing here, but it feels shady. It's karma whoring at best, and malicious at worst. We shouldn't normalize this.
I'd rather my app didn't interact with twitter without my permission
Why with Iran?
Presumably because instead of responding to the request for boobs.jpg with with an HTTP 404 error (meaning, "not found"), Iran's censorship tech returns a 403 error (meaning basically "you are forbidden from accessing this resource).
The "boobs" are "forbidden" you see; the tech mirrors the ruling party's moral stance, probably coincidentally. Trying the same curl command in Russia and China will likely just get you a 404 error, so the joke really only works with Iranian servers. The 404 version is slightly less funny: "We couldn't find the boobs!"
Hey, at least they’re using HTTP codes correctly.
It's 403 because they are upfront about the resource being censored as opposed to unavailable, and they tell you who to contact if you have legigimate reasons to access it.
First they came for the boobs...
It was annoying as hell trying to download a LaTeX compiler and having the entire word be blocked, presumably because certain degenerates use latex - the material - for immoral acts.
curl -i https://irangov.ir/boobs.jpg # HTTP 200
curl -i https://president.ir/boobs.jpg # HTTP 200
curl -i https://divar.ir/boobs.jpg # HTTP 404
Can't reproduce. The goverment websites don't even handle the error correctly: they give a HTTP 200 and an error page.
Does anyone have an actual working example?